Unified user credentials with Keycloak SSO
What is SSO (single sign-on)
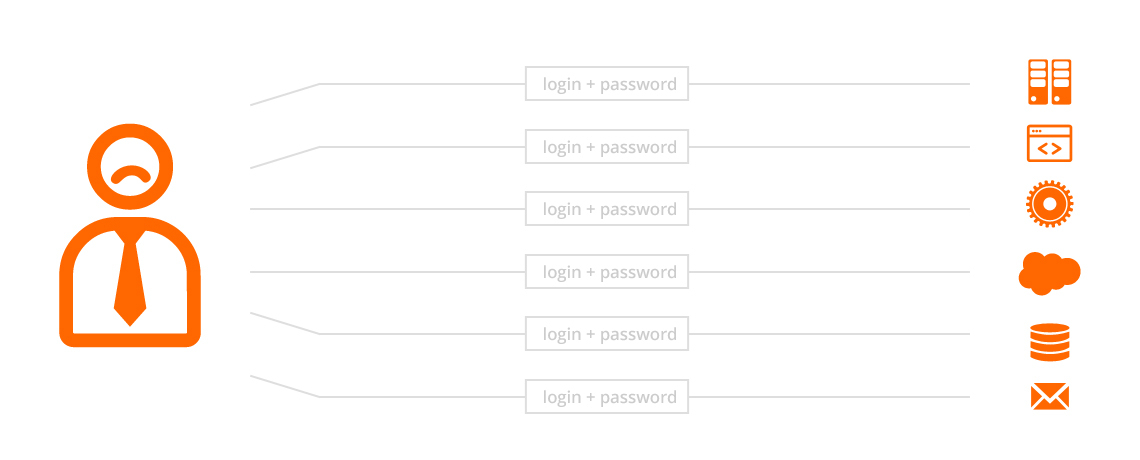
The underlying principle of SSO is that instead of remembering multiple sets of credentials (typically a user name and password for each application/service), the user only needs to remember one set of credentials. All of the other credentials are handled by an SSO system, while all of the existing security policies and requirements are still satisfied. SSO can become the gateway into multiple integrated, or even independent systems.
The reason for the invention of SSO was simple. In the real world, there is a strong pressure on various types of credentials. This is clearly ilustrated in the case of passwords, where there are various requirements on the minimum length, structure (upper and lower-case letters, special characters, digits etc.), frequency of changes or reuse of passwords and so on. But this enforced complexity is often counterproductive. Is it realistic for a regular user to remember dozens of long and frequently changed passwords? Doesn't this actually lead to circumvention of security policies?
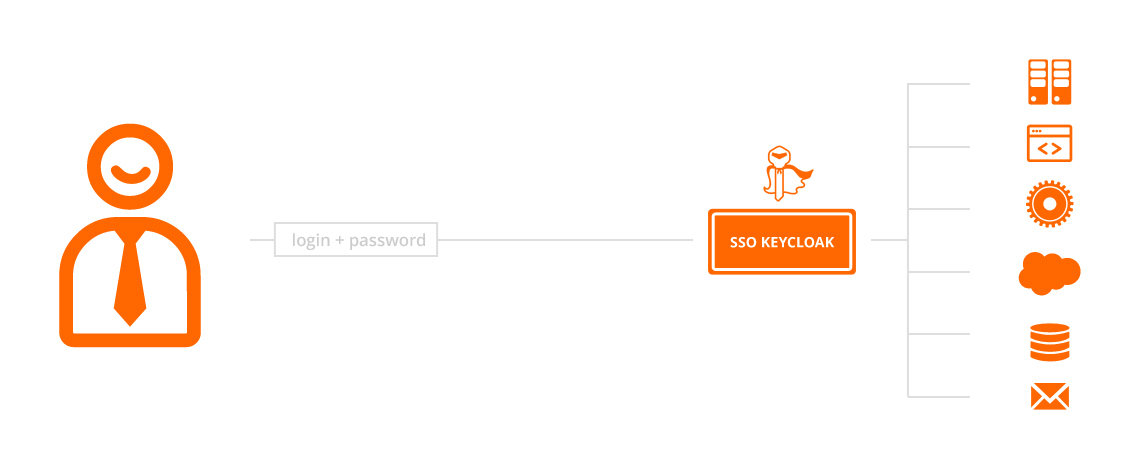
SSO addresses these issues through transparent sign-in into various systems. This allows the user to move between systems as if they were part of a single application or service. Another advantage is reduced load on the technical support team, with fewer credential related support tickets. Once the users no longer feel the need to circumvent the credential policies, security of the system improves. Last but not least, SSO makes it easier to comply with security policies and legislation.
Our single sign-on solution? Watch our short video!
What is Keycloak SSO
Keycloak is one of the best implementations of SSO. Keycloak is an Java based open-source solution with enterprise support, developed by Red Hat Software. Keycloak is a modern project, utilizing technologies such as social network login, OAuth2 and OpenShift. It includes a management console for account management, administration console and the ability to define workflows for accounts.
Keycloak can be integrated with third party products such as Active Directory, Facebook, Twitter, LDAP etc. It is possible to deploy it in a cluster (High Availability) and integrate it with existing applications using either web services or by re-skinning the SSO login page. Keycloak is able to quickly and reliably replace multiple credentials for various systems with a single sign on into all of the connected systems.
I need SSO
SSO offers the highest added value when you're using two or more applications or services which require user login (or other services which need to authorize access of your users).
The following is a list of reasons to choose SSO:
- Are your users logging into two or more applications/services?
- Will you need to sign your users into new applications/services in the future?
- Do you want to offer your users multiple different sign-in methods?
- Do you want to let your users access your systems or services more easily?
- Do you need an overview of all of your users and their roles?
- Do you want to speed up the development of new applications that require user sign-on?
- Would you like to avoid circumvention of security policies?
Try our File Explorer Demo application with Keycloak SSO login!
Why Keycloak SSO
Unlike other SSO solutions, Keycloak is free of charge, with the option to additionally purchase enterprise support. This gives Keycloak a huge advantage during deployment or when replacing an older SSO solution. The customer only needs to pay the specialists who will deploy Keycloak, and doesn't need to pay any other fees. This approach makes Keycloak the ideal SSO solution of the past few years, as is demonstrated by massive deployments at various global companies.
The following is a list of reasons to choose Keycloak SSO:
- Price - the best priced SSO solution on the market.
- Integration with an existing solution - ability to integrate Open LDAP and Active Directory through a connector.
- Modern technologies - OpenID Connect and SAML 2.0 SSO for Single Log Out for applications in the browser.
- Identities and social network brokers - ability to simply connect to Twitter, Google, Facebook etc. or to delegate requests over SAML 2.0 and OIDC.
- Security policies - ability to easily set password policies and revocations.
- Impersonation - option to sign in administrators as different users for easier and quicker troubleshooting.
- Themes - Keycloak allows easy styling of the login page, administrator console, account management console and e-mails. The whole system is fully localized.
- Modern solution - Keycloak includes a REST API for all SSO functions such as log-in, log-out, user token refresh etc.
Consult the Keycloak site for more information about the advantages of the solution.
Our solution
We offer deployment of Keycloak SSO and its integration with existing systems. We also help our clients with incorporation of services and applications, which use Keycloak for user authorization and authentication, in the form of either consulting and training, or Java development.
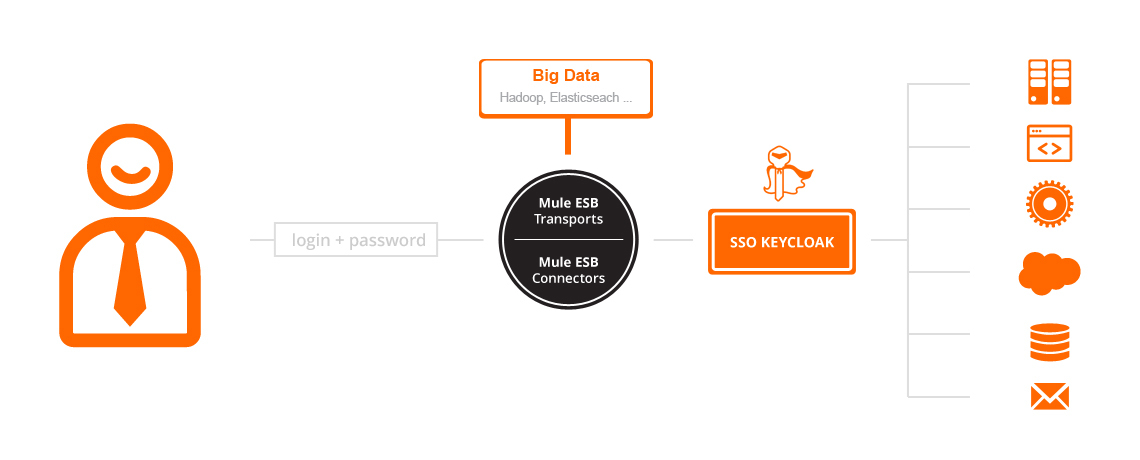
During some projects, we've also integrated Keycloak with Big Data systems, which store additional data about the users, and it is possible to further generate and analyze various data and find new sales opportunities for our clients. Calling Keycloak through Mule ESB is no exception, it can simplify the clients system infrastructure. Data retrieved from Keycloak calls can be further processed and sent into other systems directly from Mule ESB.
Some of our projects and stats
- Keycloak deployments and customizations - numerous production deployments (with customizations) delivering SSO capabilities for our customers.
- 2-phase auth - Keycloak's standalone component for 2-phase authentication of end users via sms messages and emails.
- Services security - a component with high throughput capable of authentication and authorization of http/https requests against Keycloak.
- Legacy systems connection - several components adding possibilities to authenticate and authorize against customer's legacy systems.
- Big Data federation - federation of users and roles from Elastic and OrientDB.
- Token caching - new subsystem for Keycloak capable of caching and serving SSO tokens for customer's 3rd party users and services.