Integration Eye - streamlining and monitoring of integrations, APIs and systems
What is Integration Eye
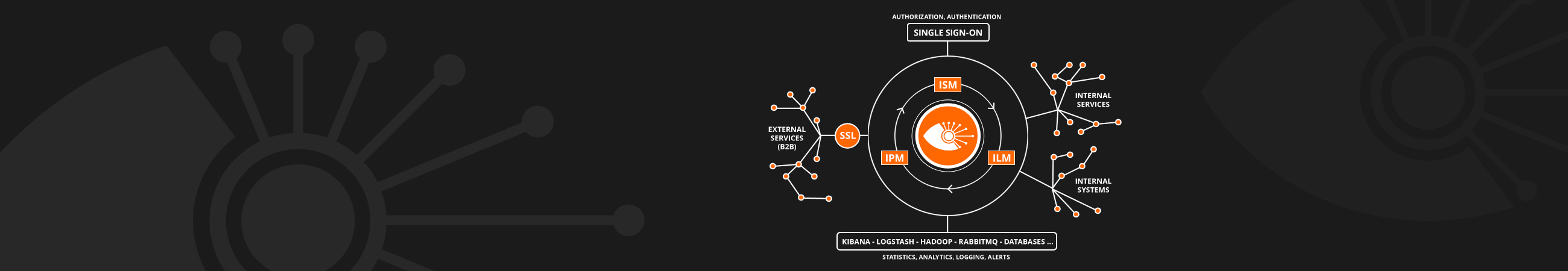
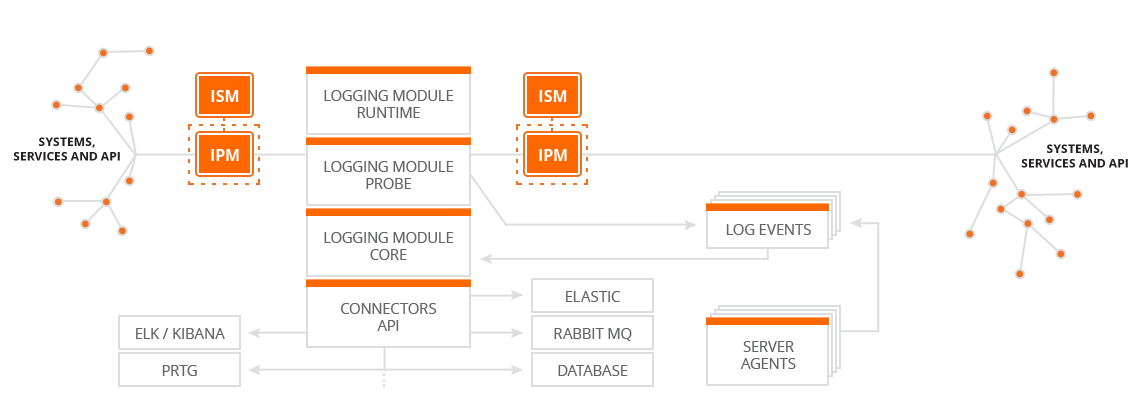
Integration Eye® is a modular product, which streamline system integrations, infrastructure and business. It consists of 3 modules: proxy module IPM, logging module ILM and the security module ISM, which can be used independently or combined. It is based on the widely used, secure and platform independent Java language (why choose Java?) and it runs on the lightweight integration engine Mule™.
Get an overview of Integration Eye products quickly. Video is worth a thousand words!
Why choose Integration Eye
Using individual Integration Eye® modules, you can monitor your APIs and systems, create statistics on and analyze calls (logging with the ILM module) and be alerted to any problems, downtime or slow responses of specific APIs and systems. You can secure your APIs and systems using roles (authorization and authentication with the ISM module) based on Keycloak SSO we deliver or your existing Auth server. You can extend or proxy service calls (both internal and external) with mutual SSL, headers, etc. (proxy with IPM) you can also monitor and analyze these calls. The IPM module streamlines service and system calls in general (for example, you will know which services are being used, and won't need to maintain unused ones).
We can deliver and deploy our tailored solution, provide subsequent support, updates, extensions or configuration changes as the customer APIs and systems evolve. We can provide training for your employees, to let them configure and administer the solution without our involvement (even though we are available whenever needed). Would you like to try it? You can visit our online documentation and demo, including installation guides and a free production Start-up license.
Individual Integration Eye® modules are backed by years of development and testing. Modules are developed since the beginning with attention to the needs of our customers, and new features are constantly being added based on their needs and feedback.
- Modularity - all modules can be freely combined.
- Development - we are constantly developing our product and adding more features, which are requested by our customers.
- Performance - we prioritize high performance of the individual modules, to avoid additional hardware costs. For example, a single instance of IPM can easily handle 5000+ requests per minute including logging using the ILM module.
- Portability - the products can run in any environment(Windows, Linux etc.) with various databases (Oracle, MySQL etc.).
- Integration - we can reliably connect Integration Eye® to your other systems (both existing and newly deployed). You can, of course, do this yourself using the online documentation and email support, which is included with every production license.
- Production tested - our products are used by customers in both Europe and USA. The products can run on-premises or in the cloud.
- Support - we support deployments, updates and offer additional consultations.
- License - each production license comes with 9 non-production licenses, you won't hit any problems with your own development and in-house testing.
- Price - unmatched prices for both the licenses and support. You only pay for the Integration Eye® modules you use.
Do you have a minute? Try our online demo with real-time data.
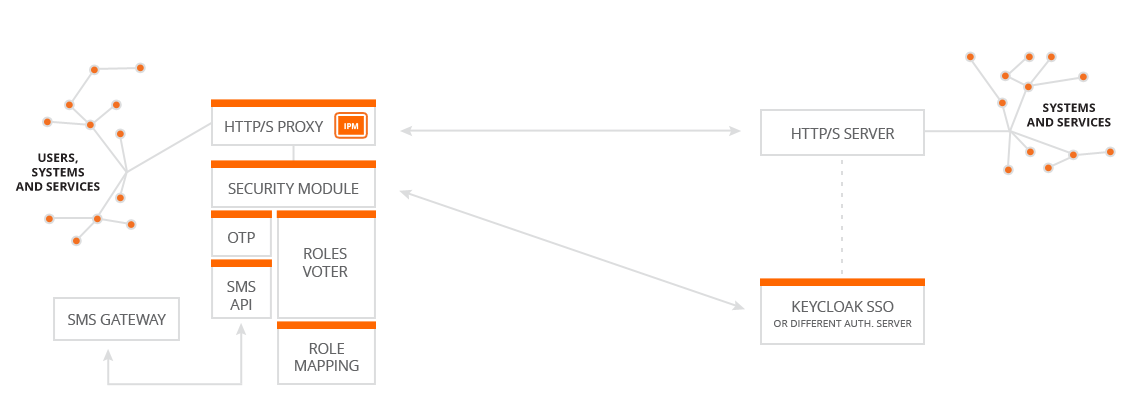
IntegrationEye Proxy Module (IPM)
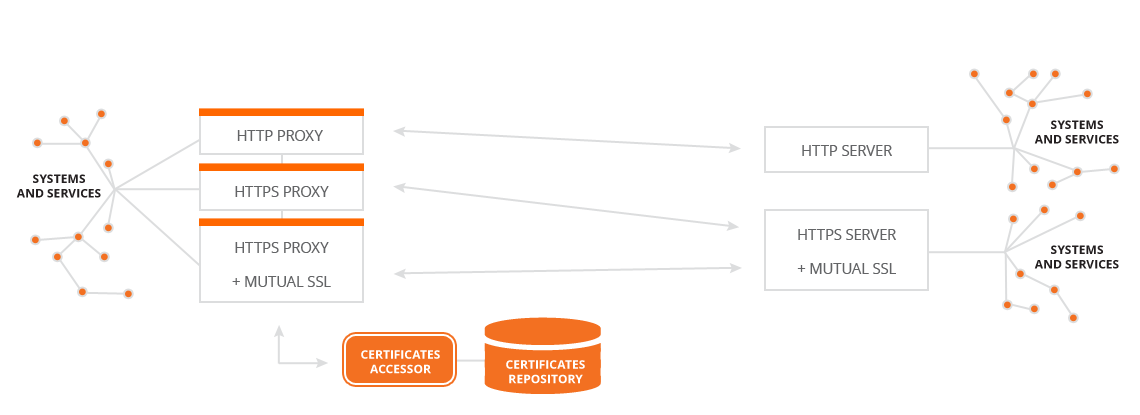
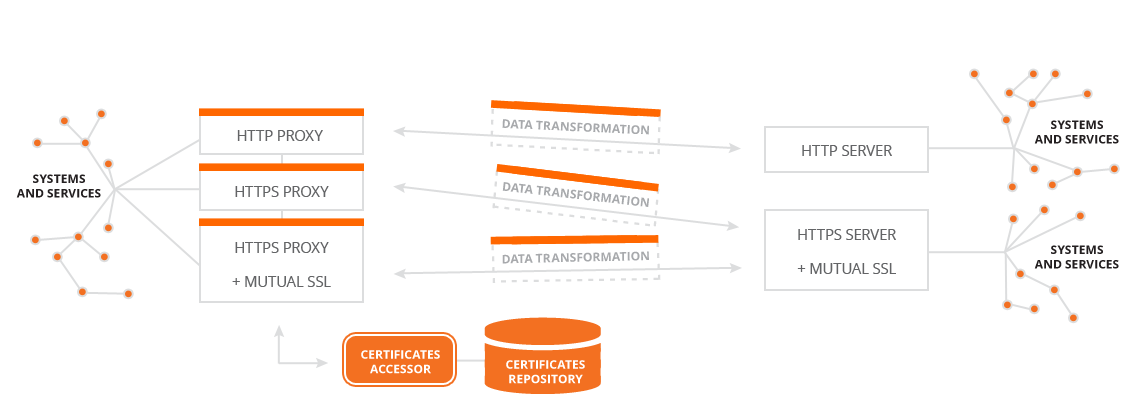
Our proxy primarily serves to streamline calls and integrations. It also supports deployment of multiple instances to provide high availability / load balancing. IPM can extend individual calls with features like additional headers or mutual SSL with automatic certificate selection. The main benefits are that all traffic crossing the proxy can be logged using ILM, and data transformations.
- Proxy core - HTTP/HTTPS proxy (including the option to transform data).
- SSL and certificates - mutual SSL proxy (including automatic certificate selection based on target URL from Keystore repository).
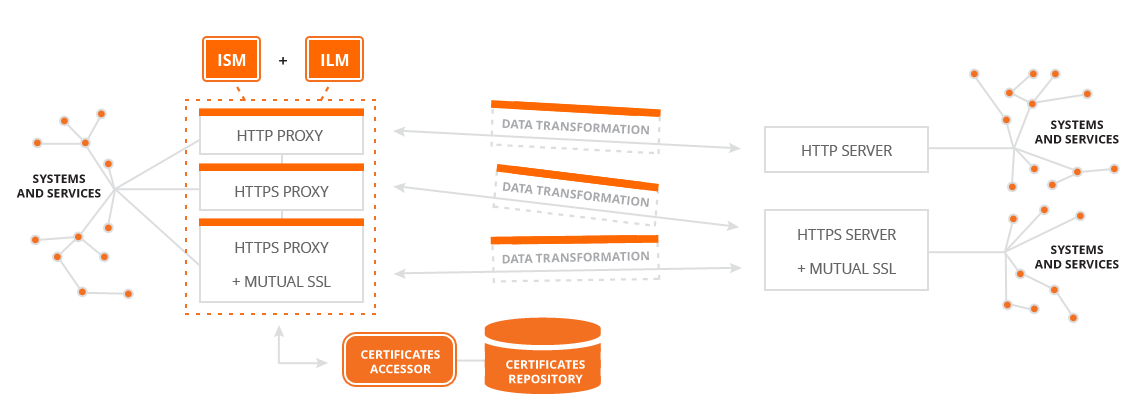
- Integration - the option to secure services with ISM and logging with ILM.
- Streamlining - overall clarification of the architecture of service calls and systems.
- Intranet gateway - the ability to run on the intranet using a defined gateway.
- Configuration - comprehensive XML based configuration.
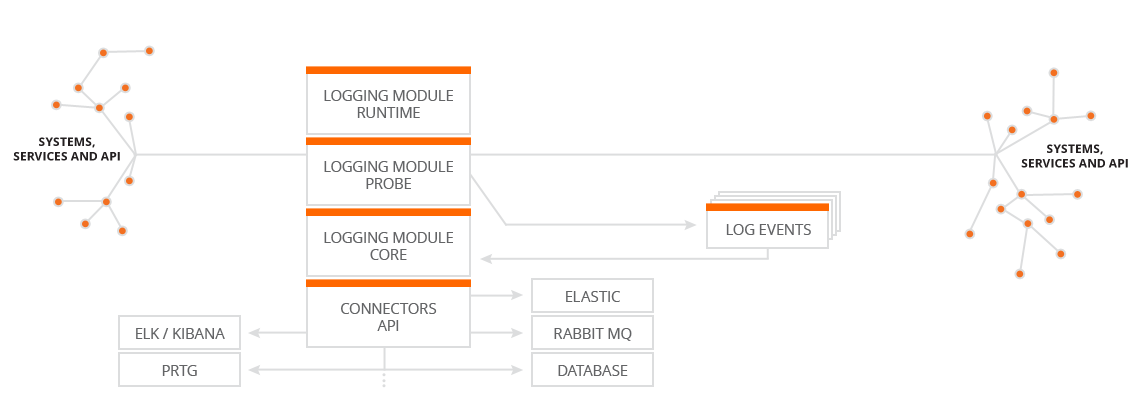
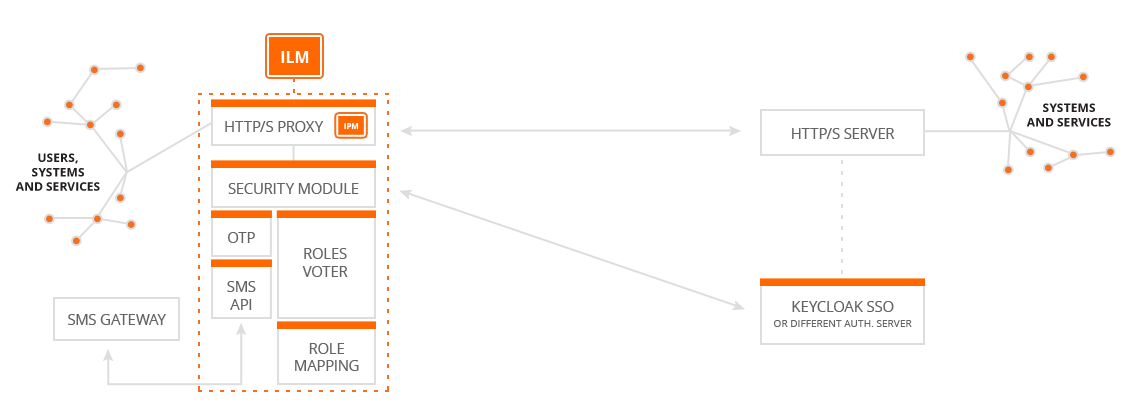
IntegrationEye Logging Module (ILM)
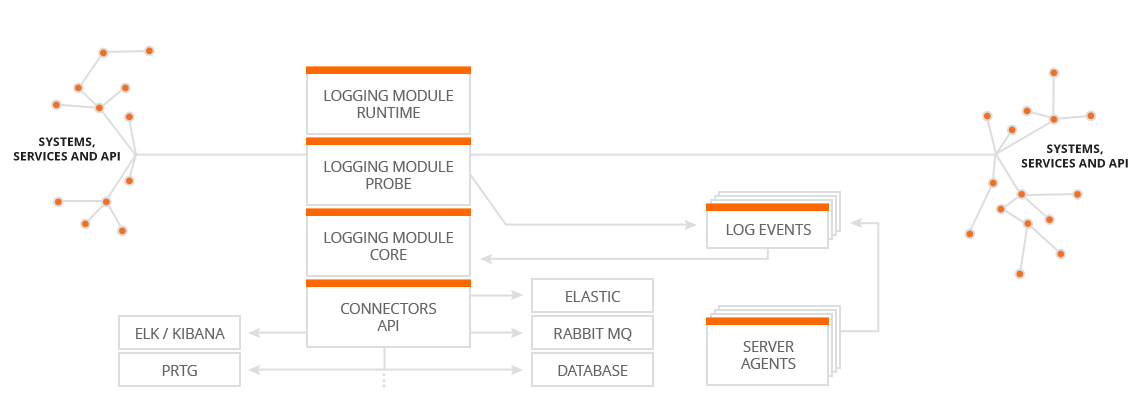
Our logging module can asynchronously write all important information about the status of service calls (you choose what is important through configuration). This allows you to easily locate a problem, be alerted about it, or to gather statistics and get a better overview. You can monitor HTTP return codes of services, call times, who is using which service (with ISM) etc. Logging can be easily connected to a large number of systems using our connectors, these can also be developed based on your needs.
- Logging core - asynchronous logging to external systems.
- Built-in connectors - connectors for Elastic, RabbitMQ, ELK/Kibana, Hadoop, Databases, PRTG etc. (option to develop any other additional connector).
- Templating - option to define your own log messages using templates (json, xml etc.) with placeholders (Java version, server name, thread name, description and type of error, correlation ID etc.).
- Stopwatch - ability to log the duration of calls and runtime of services and systems.
- Server monitoring - ability to log server status (CPU, RAM, disk utilization, number of cores etc.) using agents.
- Optimization - low CPU and RAM requirements.
- Various output formats - output formats json, xml, plain text etc.
- Robustness - ability to tolerate outages of external systems (including local storage to persist data during an outage).
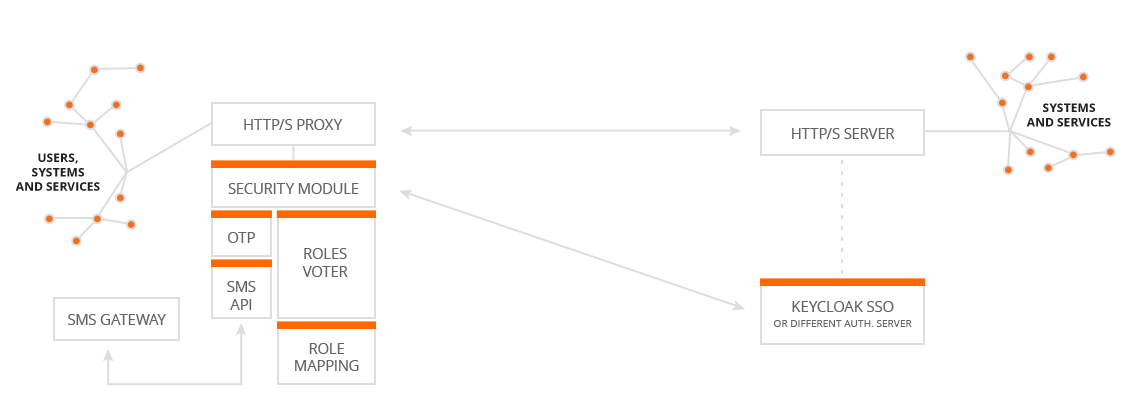
IntegrationEye Security Module (ISM)
Using out security module you can ensure security for all calls, including (legacy) services, which don't implement any security. It is also possible to improve the security using one time SMS codes (OTP) and to work with multiple Realms at once (to better separate your user groups). ISM can also be connected to your existing SSO solution. In combination with IPM and ILM, you will have complete overview of when and who (what) is calling your services and systems.
- Authentication - Basic and Bearer authentication (with the option to disable Basic - i.e. forcing the calling systems to use Bearer).
- Basic-to-OAuth - the option to get OAuth tokens based on Basic autentication.
- Selection of multiple realms or applications - the options to authenticate against multiple clients/applications and realms (configuration using XML or dynamically using HTTP headers).
- Authorization - authorization based on URL (Ant path) or on defined roles.
- OTP - OTP (One Time Password) including integration with an SMS Gateway (Eurosms and Axima or others), sending based on e.g. ISO country code etc.
- SSO integration - Integration with Keycloak SSO or other Auth server.
- Multiple sources of users - ability to authenticate against different user sources.
- Configuration - configuration using XML (ability to describe complex conditions, conditional OTP calls, OTP call limits, asynchronous calls of your own services after a successful/unsuccessful OTP call, conditional authentication and authorization and much more).